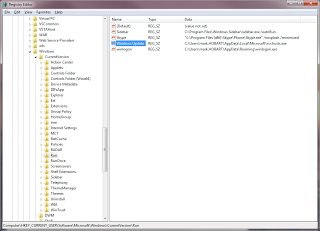
This morning, Firefox stalled while loading the login page for the ANZ Internet Banking website. Looking at the status bar, I could see that Firefox was attempting to connect to a website, australianewzealandb.tt.omtrdc.net. This raised immediate alarm bells, because I didn’t recognise the website address, and it certainly wasn’t an official anz.com sub-domain.
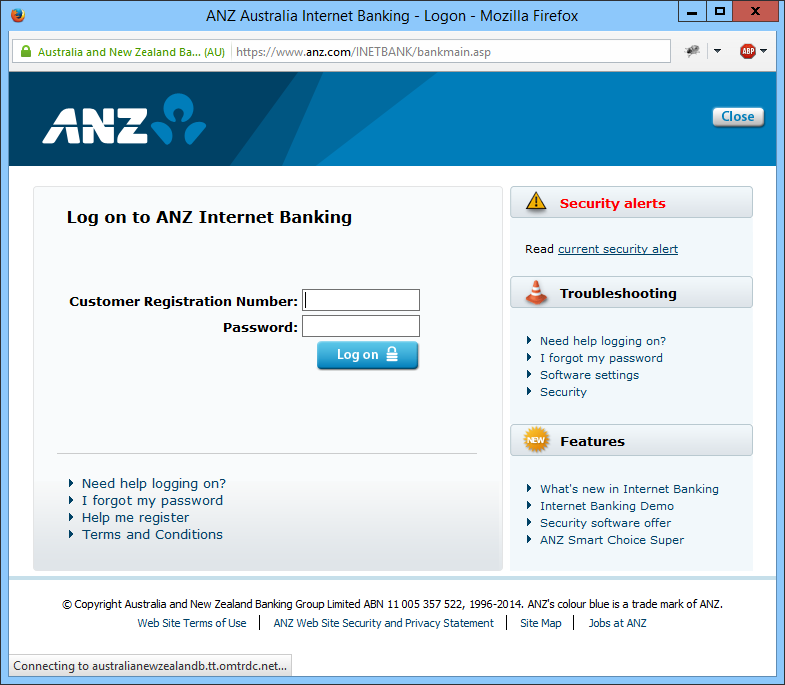
The connection eventually started, and the page finished loading — just one of those little glitches loading web pages that everyone encounters all the time, right? But before I entered my ID and password, I decided I wasn’t comfortable to continue without knowing what that website was, and what resources it was providing to the ANZ site.
And here’s where things got a little scary.
It turns out that australianewzealandb.tt.omtrdc.net is a user tracking web site run by marketing firm Omniture, now a part of Adobe. The ANZ Internet Banking login page is requesting a Javascript script from the server, which currently returns the following tiny piece of code:
if (typeof(mboxFactories) !== 'undefined') {mboxFactories.get('default').get('SiteCatalyst: event', 0).setOffer(new mboxOfferDefault()).loaded();}
The Scare Factor
This script is run within the context of the Internet Banking login page. What can scripts that run within that context do? At worst, a script can be used to watch your login and password and send them (pretty silently) to a malicious host. This interaction may even be undetectable by the bank, and it would be up to you and your computer to be aware of this and block it — a big ask!
At worst, a script can be used to watch your login and password and send them to a malicious host.
The Relief
Now, this particular script is fortunately not malicious! In fact, as the mboxFactories variable actually is undefined on this page, this script does nothing at all. In other words, it’s useless and doesn’t even need to be there! (It’s defintely possible that the request for the script is being used on the server side to log client statistics, given the comprehensive parameters that are passed in the HTTPS request for the script.)
What are the risks?
So what’s the big deal with running third party script on a website?
The core issue is that scripts from third party sites can be changed at any time, without the knowledge of the ANZ Internet Banking team. In fact, different scripts can be served for different clients — a smart hacker would serve the original script for IP addresses owned by ANZ Bank, and serve a malicious script only to specific targeted clients. There would be no reliable way for the ANZ Internet Banking security team to detect this.
Scripts from third party sites can be changed at any time, without the knowledge of the Internet Banking team.
Another way of looking at this: it’s standard practice in software development to include code developed by other organisations in applications or websites. This is normal, sensible, and in fact unavoidable. The key here is that any code must be vetted and validated by a security team before deployment. If the bank hosts this code on their own servers, this is a straightforward part of the deployment process. When the bank instead references a third party site, this crucial security step is impossible.
Banking websites are among the most targeted sites online, for obvious reasons. I would expect their security policies to be conservative and robust. My research today surprised me.
Trust
How could third party scripts go wrong?
First, australianewzealandb.tt.omtrdc.net is not controlled by ANZ Bank. It’s controlled by a marketing organisation in another country. We don’t know how much emphasis they place on security. We are required to trust a third party from another country in order to login to our Internet Banking.
This means we need to trust that none of their employees are malicious, that they have strong procedures in place for managing updates to the site, the servers and infastructure, and that their organisation’s aims are coincident with the tight security requirements of Internet Banking. They need to have the same commitment to security that you would expect your bank to have. That’s a big ask for a marketing firm.
Security
The ANZ Internet Banking website is of course encrypted, served via HTTPS, the industry standard method of serving encrypted web pages.
We can tell, just by looking at the address bar, that anz.com uses an Extended Validation certificate.
With a little simple detective work, we can also see that anz.com serves those pages using the TLS_RSA_WITH_AES_256_CBC_SHA encryption suite, using 256-bit keys. This is a good strong level of encryption, today.
However, australianewzealandb.tt.omtrdc.net does not measure up. In fact, this site uses 128-bit RC4+SHA encryption and integrity and does not have an Extended Validation certificate. RC4 is not a good choice today, and neither is SHA. This suggests immediately that security is not their top concern, which should then be an immediate concern to us!
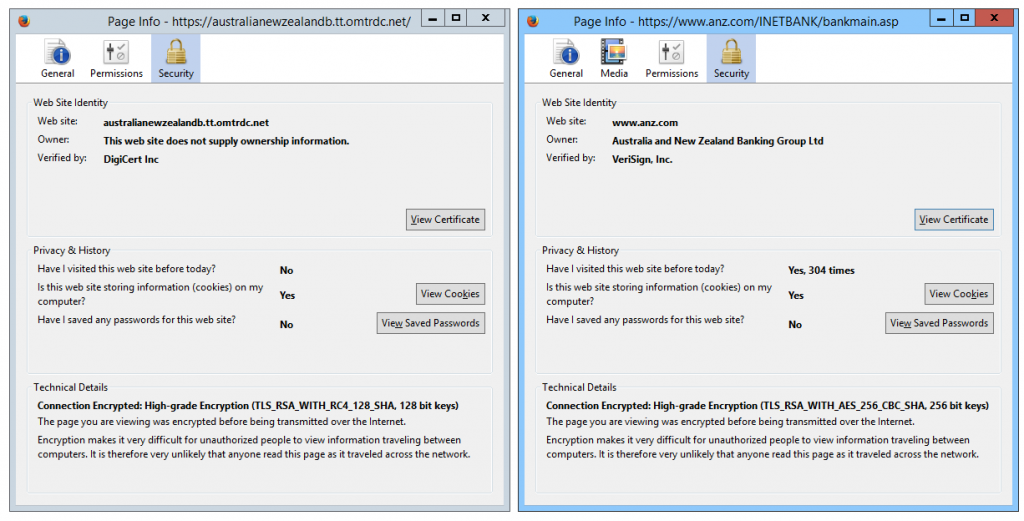
I should qualify this a little: Extended Validation certificates are not available for wildcard domains, which is the type of certificate that tt.omtrdc.net is using. This is for a good reason: “in order to ensure that EV SSL Certificates are not issued fraudulently or misused after issuance.” It’s worth thinking through that reason and seeing how it applies to this context.
Malicious Actors
So how could a nasty person steal your money?
In theory, if a nasty person managed to hack into the Adobe server, they could simply supply a script to the Internet Banking login page that captures your login details and sends them to a server, somewhere, anywhere, on the Internet. This means that we have to trust (there’s that word again) that the marketing firm will be proactive in updating and patching not only their Internet-facing servers, but their infrastructure behind those servers as well.
If a bad actor has compromised a certificate authority, as has happened several times recently, they can target these third party servers . Together with a DNS cache poisoning or Man-In-The-Middle (MITM) attack, even security-savvy users will be unlikely to notice fraudulent certificates on the script servers.
 Security flaws like Heartbleed are exacerbated by this setup. Not only do the bank security team have to patch their own servers, they also have to push the third party vendors to patch theirs as a priority.
Security flaws like Heartbleed are exacerbated by this setup. Not only do the bank security team have to patch their own servers, they also have to push the third party vendors to patch theirs as a priority.
Protect Yourself
As a user, run security software. That’s an important first step. Security software is regularly refreshed with blacklists of known malicious sites, and this will hopefully minimize any window of opportunity that an untargeted attack may have. I’m not going to recommend any particular brand, because I pretty much hate them all.
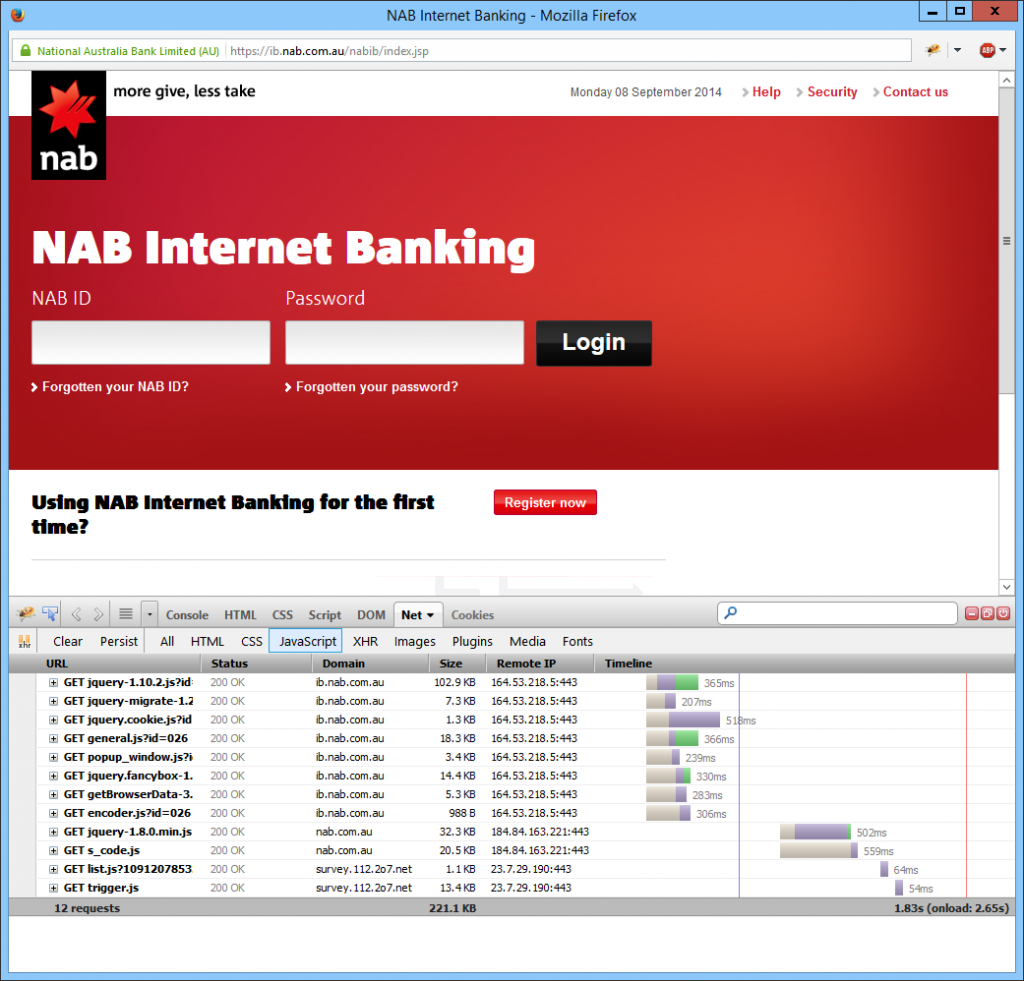
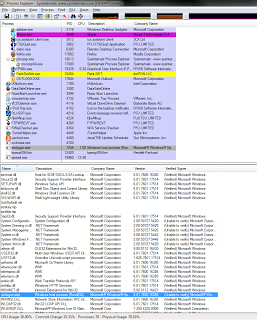
If you want to unleash your inner geek and be aware of how sites are using third party script servers, you can use Developer Tools included in your browser — press F12 in Internet Explorer, Chrome or Firefox, and look for the Network tab to see a list of all resources referenced by the site. You may need to press Ctrl+F5 to trigger a ‘hard’ refresh before the list is fully populated.
I’ve shown below the list of resources, filtered for Javascript, for the National Australia Bank Internet Banking site. You can see two scripts are loaded from one site — again, a market research firm.
Simplistic Advice for Banks
Specifically to mitigate this risk, banks should consider the following:
- Serve all scripts from your own domain and vet any third party scripts that you serve before deployment.
- In particular, check third party scripts for back end communication, via AJAX or other channels.
- Minimize the number of third party scripts anywhere that secure content must be presented.
- Use the Content-Security-Policy HTTP header to prevent third party scripts on supported browsers (most browsers today support this).
There are of course other mitigations, such as Two Factor Authentication (2FA), which do reduce risk. However, even 2FA should not be considered a silver bullet: it is certainly possible to modify the login page to take over your current login in real time — all the user would see is a message that they’d mistyped their password, and as they login again, the malicious hacker is actively draining money from their account.
A final thought on 2FA: do you really want a hacker to have your banking password, even if they don’t have access to your phone? Why do we have these passwords in the first place?
Browser Developers
I believe that browser vendors could mitigate the situation somewhat by warning users if secure sites reference third party sites for resources, in particular where these secure sites have lower quality protection than the first party site. This protection is already in place where content is requested over HTTP from a HTTPS site, known as mixed content warnings.
There is no value in an Extended Validation certificate if any of the resources requested by the site are served from a site with lower quality encryption! Similarly, if a bank believes that 256-bit AES encryption is needed for their banking website, a browser could easily warn the user that resources are being served with lower quality 128-bit RC4 encryption.
Australian Banks
After this little investigation, I took a quick look at the big four Australian banking sites — ANZ, Commonwealth Bank, National Australia Bank, and Westpac. Here’s what I found; this is a very high-level overview and contains only information provided by any web browser!
| Bank | Bank site security | # 3rd party scripts | Third party sites | Third party security |
|---|---|---|---|---|
| ANZ Bank | 256-bit AES (EV certificate) | 1 | australianewzealandb.tt.omtrdc.net | 128-bit RC4 |
| NAB | 256-bit AES (EV certificate) | 2 | survey.112.2o7.net | 256-bit AES |
| Westpac | 128-bit AES (EV certificate) | None! | ||
| Commonwealth Bank | 128-bit AES (EV certificate) | 9! | ssl.google-analytics.com | 128-bit AES |
| commonwealthbankofau.tt.omtrdc.net | 128-bit RC4 | |||
| google-analytics.com | 128-bit AES | |||
| d1wscoizcbxzhp.cloudfront.net | 128-bit AES | |||
| cba.demdex.net | 128-bit AES |
Do you see how the *.tt.omtrdc.net subdomains are used by two different banking sites? In fact, this domain is used by a large number of banking websites. That would make it an attractive target, wouldn’t you think?
I reached out to all 4 banks via Twitter (yeah, I know, I know, “reached out”, “Twitter”, I apologise already), and NAB was the first, and so far only, bank to respond:
@MarcDurdin Hi Marc, I'm keen to have our tech team look into this for you – could you pls DM me more details? ^TC
— NAB (@NAB) September 8, 2014
Kudos are due to NAB and Westpac — NAB for responding so promptly, and Westpac, for not having the issue in the first place!
Updates (6:10am, 9 Sep 2014), with thanks, in no particular order:
Many thanks to Troy Hunt for suggesting I write this, then tweeting it — and for his continual and tireless work in websec!
Stefano Di Paola mentioned a previous Omniture vulnerability and referenced 3rd party script risks in his blog:
.@troyhunt @MarcDurdin 3rd p. JS:/ Omniture past: http://t.co/BRgRJWnNYb and another (fixed,unpublished) that led to DOMXSS b/c of dbg param
— Stefano Di Paola (@WisecWisec) September 8, 2014
hillbrad⚡ mentioned a W3C project to make validation of sub-resource integrity possible:
@troyhunt @WisecWisec @MarcDurdin working on it: http://t.co/8FjN6DTTCT
— Brad Hill (@hillbrad) September 8, 2014
Erlend Oftedal reminded me that this is not a new issue and mentioned his blog post from 2009:
@troyhunt @MarcDurdin Agreed. Shameless plug from 2009: http://t.co/5lQlfkEPq4
— Erlend Oftedal (@webtonull) September 8, 2014