Another Five Things Story, for my girls. Just need an illustrator now and I can retire.
One of the girls (I honestly can’t remember which) gave me these five things to incorporate into the story: Talking Penguin; magic stone; tree; red eel; blueberry bush, and a special request that Daniel Higginbottom make an appearance. If you can bear to read it, here’s the result.
The first episode, Daniel Higginbottom and the Hairbrush, is buried in my blog about my holiday with Hannah.
Daniel Higginbottom and The Penguin
Talking Penguin; magic stone; tree; red eel; blueberry bush
Daniel Higginbottom woke up, got up, and got dressed. He got into his normal, boring work clothes. Then he ate his normal, boring breakfast cereal and read his normal, boring newspaper. After brushing his teeth, with his normal, boring toothbrush, he got into his normal, boring, brown car and drove to his normal, boring office at the government’s Treasury Building, where he worked as an accountant.
He drove into the carpark under the office building, and took the lift up to his office, and here he stopped being quite so boring, because he immediately saw a note on his desk saying, “Come to my office at once. S”.
He knew who S was. Do you?
Without delay, Daniel strode down the hallway to S’s office, and knocked upon the fancy door. “Come in,” came the call, and Daniel opened the door and walked into the office, treading upon the deep pile carpet and coming to a standstill in front of the fine walnut and oak desk behind which, in a large and comfortable chair, sat S, the Spy Master.
“Daniel, I have a new mission for you,” started the Spy Master. At this point, no doubt you realise that Daniel was not quite what he seemed. In fact, Daniel was a really truly spy. And he’d already had many missions, including most recently one to the neighbouring kingdom to capture nothing less than a talking hairbrush!
While we were learning a bit more about Daniel, the Spy Master had continued talking, so we’ll have to go back a bit so we don’t miss anything. “This mission will be as hard as any you have ever undertaken. You must travel in our top secret spy plane to the next kingdom but three, and there locate a priceless magic stone, which we believe will be guarded by a talking penguin!”
Daniel was a little nonplussed. Why did he keep getting missions to, well, not to put too fine a point on it, steal magical objects from other kingdoms? Magical stones, magical hairbrushes? Well, he was not one to argue, and of course this was his job. So he took a deep breath, turned on his heel and strode straight back to the lift, and down to the carpark.
On the way down in the lift, he closed his eyes, and composed himself, and when he opened them, he was no longer Daniel Higginbottom, but now was Fred Smith, spy extraordinaire! I know that Fred Smith sounds like a very boring name, but Daniel was smart, and knew that a good cover name had to be boring so that people would not suspect that he was a spy!
Even though Daniel-Fred was smart, he knew he had to have something special to drive. A spy simply couldn’t drive a boring brown car. Nothing less than a red sports car would do. And a red sports car was what Daniel jumped into, and tore out of the car park in, on his way to the airport.
At the airport Daniel parked in a secret car park just for spies (no, I’m not telling you where it is), and raced over to the hangar where the top secret spy plane waited, engines fuelled and turning over, for him to climb into. As he stepped into the cabin, the door closed behind him and the plane eased its way out of the hangar and taxied straight to the nearest runway and took off. Spy planes get some special treatment at airports.
Soon, all too soon, the plane was descending to land in the next kingdom but three. Daniel had read his dossier on the mission and flushed it down the toilet in the airplane. He hoped that wouldn’t cause any problems but he simply couldn’t have it falling into enemy hands.
At the airport, the top secret spy plane, now posing as a fairly ordinary business jet plane, taxied to the business terminal and Fred (as we must now call him), looking like a normal and simply too-boring-for-words businessman, walked through the terminal and picked up his rental car – not a red sports car, sadly, but a too-appropriate-to-be-quite-nice expensive sedan car.
Fred drove to his hotel, and as the day was already drawing to a close, ate dinner and went to bed. How boring! The next morning, one might have thought that he’d forgotten his real job as he ate a boring breakfast while reading a boring newspaper (although not his normal paper as that could have given him away). But behind his newspaper, Fred’s mind was racing. How could he find this magical stone? Where would a talking penguin be kept? And why had he never heard of either of these things?
After some thought, and after finishing the comic section of the newspaper, he decided to go to the zoo. He dressed in some zoo-going clothes (don’t you have special zoo-going clothes?), climbed into his too-appropriate-to-be-quite-nice expensive sedan car, and drove down to the zoo, which was quite some distance from his hotel and the airport.
It took him no time at all to find the penguin enclosure, and after making side trips to the lions, the badgers and the emus, to make sure any potential tails would be well and truly lost and confused, he entered the enclosure. He stood watching the penguins, which seemed like completely normal and completely untalkative penguins, and wondered what to do next.
Suddenly he became aware that the man standing next to him was behaving surreptitiously. And surreptitiously handing him a note. Daniel—I mean Fred—took the note equally surreptitiously and the man surreptitiously wandered away, not looking anything like someone who had just engineered a clandestine note pass. Fred used his spy skills to read the note without being noticed.
To the rear of this building lies a blueberry bush. Under this bush lies a door. This message will self-destruct in 10 seconds.
“Oh dear,” thought Fred. He’d encountered self-destructing messages before and they were always a real pain – sometimes literally!
Sure enough, the note caught fire and burnt up rapidly, without smoke, and basically disappeared. Fred was ready though and let it drop as the last piece disintegrated, and saved his fingers from being burned, this time.
When he was sure that the coast was clear, Fred exited the building and quickly located the blueberry bush. Glancing around, and seeing no one watching, he reached under the bush and found the trap door that he now expected. As the door opened with a quiet whoosh of escaping air, he did stop to ponder just how that man knew he’d be in the penguin enclosure, and whether he should be trusting this stranger, or not! Maybe he had learned something from his previous adventure (see Daniel Higginbottom and the Hairbrush)! Or had he?
As Fred had no other leads or ideas, he climbed into the open trapdoor, and rapidly descended the tall flight of steel rungs to the bottom of the well. The trapdoor hissed closed above him, and glaring electric lights clicked on, one after another, all the way down the long corridor that opened up in front of him.
A deep hum could be heard. Fred figured that perhaps that was the pump equipment for the penguin enclosure. (See, I told you he was smart.) Without a pause, he strode down the hall way, now looking kinda spy-like, because you simply can’t look ordinary, no matter what you do, when striding down a secret passage hidden under a blueberry bush.
Soon he came to a door. It had a porthole in it, and Daniel carefully peeked in. SNAP! A glimpse of jaws filled the porthole and disappeared! That looked suspiciously like a penguin’s jaw, thought Fred-Daniel. This was clearly his destination. “This is just a little too easy,” he thought.
He looked into the porthole again. No sign of the penguin now, but the room was quite dark. Easing open the door, he squeezed in the gap, and quietly closed the door again. He turned on his toothpaste, and with the light examined the room. He stood in a large room, with a big pool at one end, and a bench with what looked like aquariums to one side. Apart from that, on the far side of the pool, was a small pedestal with something glowing and pulsating gently sitting on top. No prizes if you guess what that was!
But between the pedestal and Daniel was the pool, and in the pool was what certainly appeared to be a ferocious penguin. Never one to be frustrated long, Daniel (we might as well forget his Fred persona for now) crept over to the aquariums and looked in. Expecting fish, he was surprised to see them filled with red eels instead – and had an idea!
Carefully he pulled out a plastic spondoolickle from his spy toolkit, and gently used it to capture a single wriggling red eel. The eel looked decidedly electric and dangerous! He carried the eel over to the big pool and just as he was about to drop it in, was interrupted by a cry!
“Mon, what are ye doin’! Ye’ll kill that poor eel!”
Daniel didn’t miss a beat. He looked straight at the penguin, and sure enough, it was clambering out of the pool and waddling straight for him. It was a very large penguin indeed, he saw now, as at it came closer, and grabbed his spondoolickle with his flipper, and carried the poor eel back to the aquarium. Daniel now did miss a beat. That was so unexpected that he stood there somewhat flabbergasted.
The penguin dropped the eel back into the aquarium, and as the eel swam gratefully away, the penguin turned and slid on its tummy back to Daniel, pulling a gun out of its side as it slid! All of a sudden Daniel realised that this penguin wasn’t a penguin at all, and as the penguin handcuffed Daniel’s hands behind his back, he wondered how he could have been so easily fooled by a man in a penguin suit.
The penguin-man pushed Daniel out the door, and down the electric-light-corridor, and into a cell. The door slammed closed and Daniel sank to the floor. It wasn’t that long ago that he had been stuck in a cell but this time he didn’t expect any quick escape. How on earth could he have been so foolish? How could he have trusted that man from the enclosure? And why didn’t he secure the room with the eel and penguin before proceeding? It was all in his spy-craft course.
Time passed. Daniel thought upon his mistakes, but could not stop thinking about that man from the enclosure. So much hinged on his presence – how did he know about Daniel? And how did he know about the blueberry bush? Surely … maybe … no, Daniel couldn’t figure it out. He’d nearly nodded off to sleep when he heard a scratching noise at the door.
With a creak the door swung open. And there stood the man from the enclosure! “Follow me, and don’t make a noise,” he hissed. Daniel followed him. After all, given the choice of a sleep in a dark, dank cell, or escaping with an unknown and potentially dangerous stranger, which would you do? Okay, perhaps you’d stay in the cell, but Daniel was a spy!
They raced back along the corridor, and ducked into the penguin-eel room. It was now deserted, apart from a large number of red eels swimming in aquariums. Daniel dove into the pool, swam across to the pedestal and grabbed the pulsating stone, while the penguin-enclosure-man waited. Then, back out, up the rungs of the ladder in the well, and out the trapdoor under the blueberry bush. It was nearly dark, and the zoo was closed. The penguin-enclosure-man led Daniel to the zoo wall, where they quickly found an overhanging tree, and with standard spy-skills they swung over the wall, no problems.
The man led Daniel to a motorbike, and they both jumped on and raced away. Too late, Daniel realised that he could have run to his car and left. But, yes, it was too late. They zoomed through the city and finally turned into a garage. The garage door closed behind them, and they both climbed off the motorbike.
“Wait here,” instructed the penguin-enclosure-man, and he walked through a door. Daniel waited. What else could he do?
Moments later, the man returned, with a gun. “Oh of course,” thought Daniel, “that would have to happen.” The man grabbed the pulsating and glowing stone from Daniel and disappeared through the door again.
Daniel looked around. What resources did he have? What could he use? He examined the door and realised it wasn’t a fortified door but just an ordinary old house door. It was locked, but he could pick that lock in seconds. Now he was on a roll! He grabbed a lock-pick from his spy kit, picked the lock, in seconds, and jumped back on the motorbike. Revving it up, he drove down the hallway that was visible behind the wide open door, and into what looked like a lounge room at the end. The penguin-enclosure-man was in the room, handing the stone to a woman. Daniel drove the motorbike between the astonished pair and reached out and grabbed the stone! Without slowing, he drove the motorbike straight through the big glass window and, engine roaring, jumped onto the street! As he landed the motorbike, bending his knees to absorb the shock, he revved the engine again and pulled a big skid as he roared off down the street and to freedom!
As he ducked and wove through the late evening traffic, he thought back to the woman he’d seen. He’d caught only a glimpse in the seconds he’d been in the room, but he could have sworn it was Madelina Brompton! But there was no time to consider the implications, for in his rear view mirror, he saw a rapidly approaching black car, chasing him down! Just as well he was on a motorbike. Redoubling his ducking and weaving, he opened up the throttle and made a beeline for the airport.
How do you make a beeline for the airport? In a plane it’s easy, but it is anything but easy on a motorbike, in traffic, with a black car chasing you. But it was not for nothing that Daniel was a spy, and he finally raced into the airport, quickly parked the motorbike, raced through the terminal and out to the top secret spy plane (posing, as you recall, as a fairly ordinary business jet).
As he hurtled up the stairs to the plane, he heard an almighty crash in the distance and looked back to see the black sedan smashing through the airport gates and onto the tarmac far away on the other side of the airport. The top secret spy plane taxied out of the hangar and down to the runway. But this time it was a fairly ordinary business jet, and had to wait. The car came closer and closer. Daniel muttered quietly under his breath. Surely he’d be safe! Finally they taxied onto the runway and started taking off, with the black car chasing behind the plane!
Racing down the runway, engines screaming, the plane shuddered as it tried to take off. The driver leaned out of the car window, as it chased dangerously down the runway after Daniel. He was shaking his fist, which Daniel thought was strangely ineffectual and as the plane finally lifted into the air and he relaxed in his ever-so-comfortable top secret spy plane chair, he looked down at the rock now sitting on the table in front of him, still pulsating and glowing. What was the rock for? What made it so special – apart from the pulsating and glowing, that is? He’d probably never know.
They landed without incident at their home airport, and Daniel drove his red sports car back to the office, went back up the lift and went to see S. As he handed the rock over, S said, “Well done! I am somewhat surprised that you came back with this rock, but good work all the same! Take a couple of days off and enjoy yourself!”
Daniel went back to the car park, got into his boring brown car, and drove home. A couple of days would be good, but he wasn’t sure if it was enough time to think through all that had happened on this very action-packed mission.
THE END
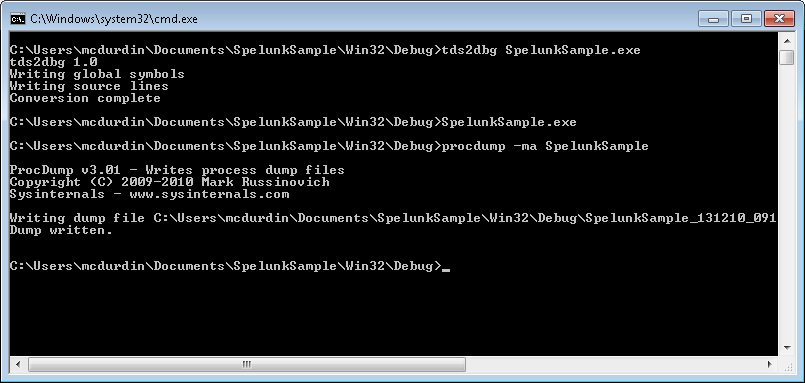
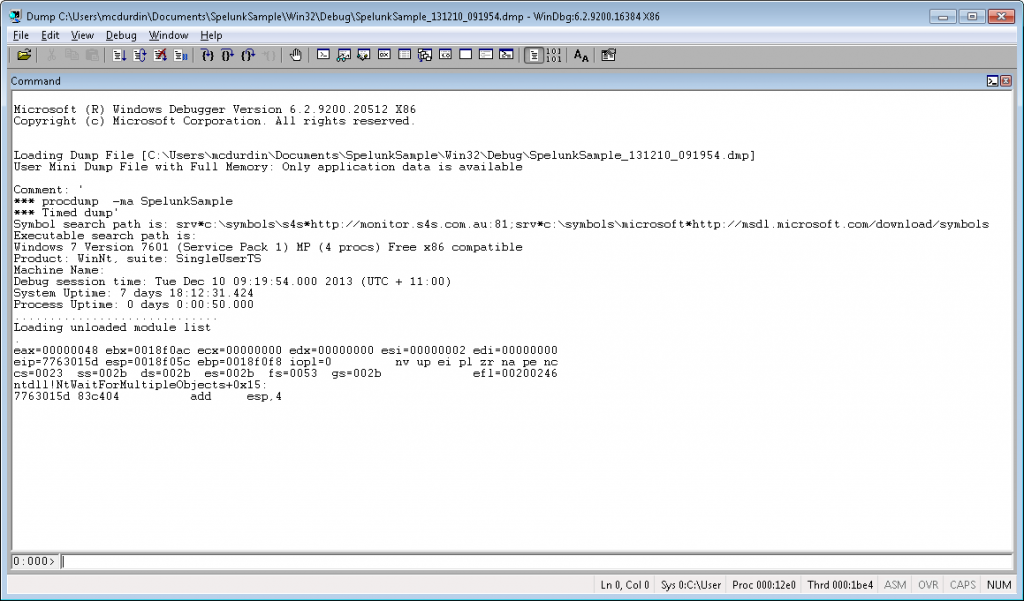
 In the midst of the twisted roadways runs the river, and across its waters lies a bridge. Call it London Bridge. Not designed. Just happened. And always growing, this way and that way, a feature here, don’t like that one there any more, should bring this railing up to spec, cries the engineer, whilst beside him the others hammer together the new houses that crowd the bridge’s fragile shoulders, and yet again it crumbles, down into the rushing waters, patched even as it falls, and saved at the last moment by the railing that the engineer brought up to spec. But touch not the railing now, lest the whole bridge collapse. Heedlessly, the crowds continue to cross the bridge.
In the midst of the twisted roadways runs the river, and across its waters lies a bridge. Call it London Bridge. Not designed. Just happened. And always growing, this way and that way, a feature here, don’t like that one there any more, should bring this railing up to spec, cries the engineer, whilst beside him the others hammer together the new houses that crowd the bridge’s fragile shoulders, and yet again it crumbles, down into the rushing waters, patched even as it falls, and saved at the last moment by the railing that the engineer brought up to spec. But touch not the railing now, lest the whole bridge collapse. Heedlessly, the crowds continue to cross the bridge.