I was recently made aware of the design of the Huntingfield Roundabout at the end of the new Kingston bypass. This new roundabout incorporates a bicycle lane around the outside. Incorporating bicycle facilities in the new road design is fantastic news, except for one big problem: around the world councils and road authorities are removing bicycle lanes from roundabouts for safety reasons1, and encouraging a dual approach, depending on the confidence level of the cyclist:
- Either leave the road and negotiate the roundabout via pedestrian crossings, or,
- Merge with car traffic when approaching the roundabout, and negotiate the roundabout in the centre of the vehicle lane.
Unfortunately, the Huntingfield Roundabout has a really strange compromise: bicycle lanes around the outside, but cyclists must give way to car traffic exiting the roundabout at each exit. That means that bicycles are giving way to traffic approaching them from behind! Perhaps this was in response to problems with a bike lane where cars give way to cyclists, but in my view this approach is just as dangerous.
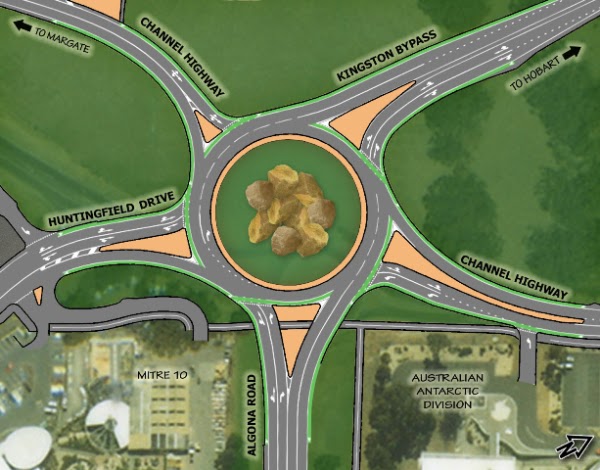 |
| Bicycle lanes on the new Huntingfield Roundabout |
I just can’t see how this design is going to be safe:
- While it’s certainly possible for a cyclist to give way, it’s counter-intuitive to how a roundabout normally works when driving a car, and so unless all cyclists are aware of the special rules for cyclists in the roundabout there’s definitely a real risk of collision when they fail to give way.
- But a similar problem applies for car drivers who are not aware of these unusual rules: they would give way to a cyclist that was about to cross their exit, which leads to an ambiguous situation and causes risks for other drivers and the cyclist who will not be expecting it.
- Moreover, this special cyclists-give-way-to-traffic-behind-them rule will lead to drivers unconciously driving in the same way at other intersections, overtaking a cyclist and immediately turning left in front of them, causing T-bone accidents. This is already an issue today, but adding new and confusing road rules will exacerbate it!
- Update (28/11): One of my friends (who happens to design bike lanes for a living) noted that cars would tend to stop on top of the bike lane when waiting to enter the roundabout.
- Finally, I (and many other riders) would tend to avoid the bike lanes anyway, both because of the frustration of stopping potentially 4 times just to get around the roundabout, and also because one is more visible when riding within the traffic lane at a roundabout. But this will cause resentment amongst drivers who just see a cyclist not using the bike lane! (Stop 4 times? Yes, a common lunch time loop ride goes up Channel Highway, round the roundabout, and back again down the highway).
It’s probably a little late now, but I wish the relevant authorities would reconsider this design!
If you are keen, here’s another opinionated post on Kingston’s on-road bicycle facilities!
(Yes, of course, with help from Wikipedia and other sources):
[1] R. Schnüll, J. Lange, I. Fabian, M. Kölle, F. Schütte, D. Alrutz, H.W. Fechtel, J. Stellmacher-Hein, T. Brückner, H. Meyhöfer: Sicherung von Radfahrern an städtischen Knotenpunkten [Safeguarding bicyclists in Urban Intersections], Bericht der Bundesanstalt für Straßenwesen zum Forschungsprojekt 8952, 1992